According to an article in its company blog, the security company Kaspersky Lab has uncovered one of the biggest malware infections of recent years. According to the company, the antivirus software was able to detect malware on more than 57,000 computers, which a hacker had smuggled into a server of the Taiwanese hardware manufacturer ASUS. The previously unknown perpetrator, in the action called ‘Operation ShadowHammer’ by Kaspersky, has hidden his malware in the software ‘ASUS Live Update Utility’ and distributed it to Asus customers who wanted to obtain this software directly from the company’s download page.
According to Kaspersky, the malware was distributed via ASUS software from June to November 2018, and ASUS was informed of the infection of its update server on January 31, 2019.
Symantec confirms infections
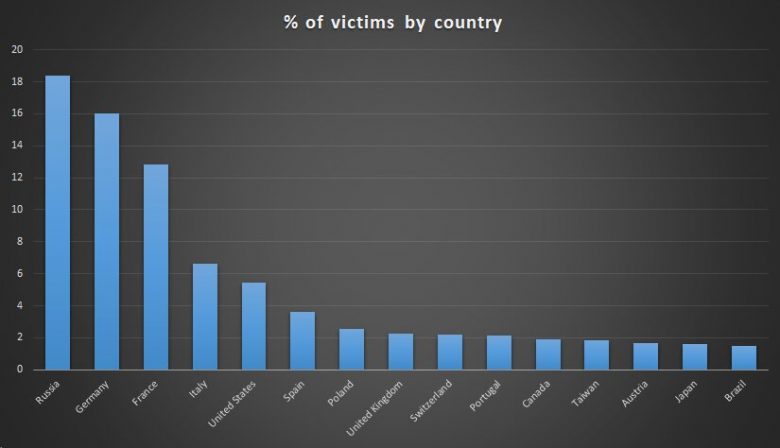
Kaspersky extrapolated the distribution of infected computers by country from the 57,000 or so computers from which the antivirus software removed the malware. The number of infected computers, which according to Kaspersky exceeds one million, was also extrapolated from the antivirus software data.
The security company Symantec also confirms that the malware operation discovered by Kaspersky exists. The company’s antivirus software has detected malware on more than 13,000 systems, as a spokesperson for the magazine Motherboard confirmed.
BIOS/UEFI, software and driver updates
In fact, the software misused by hackers can be used to update the BIOS/UEFI, software and drivers of ASUS computers and laptops. The hackers also distributed the malware with the meaningless name ‘setup.exe’ via the update tool, which was supposed to be an update for the software itself.
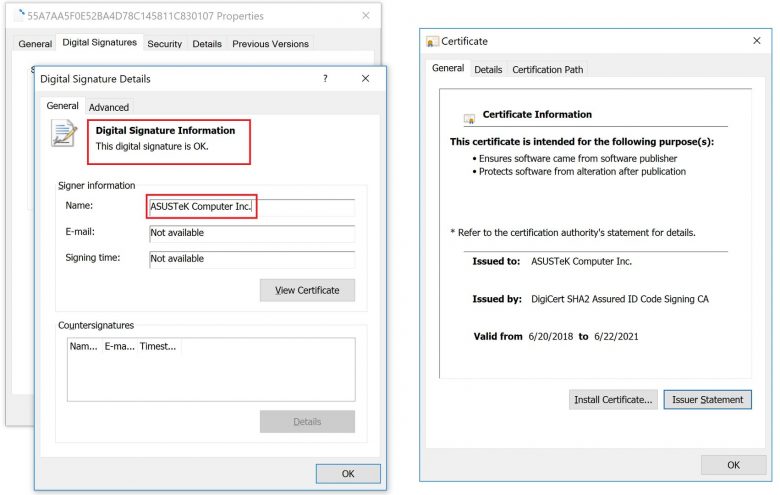
Digital signature stolen from ASUS
Since the software was a file created by ASUS three years ago and into which the hackers merely injected the malware, the digital signature continued to display the ASUS certificate. The use of ASUS’ digital signature may also be the main reason why the hardware manufacturer has not noticed the infection for so long.
According to Kaspersky, the hackers were able to re-sign the manipulated file because they obtained two original ASUS certificates. During the infection, the signature was renewed once because the originally used certificate had expired. Kaspersky points out gross security breaches, because ASUS has used the certificate for another month after the company was informed about the abuse by the hackers, instead of deactivating it immediately and making it unusable for the hackers.
attack on selected computers
Although the attackers distributed the malware to a gigantic number of computers, according to Kaspersky, individual systems were deliberately attacked. Kaspersky found 600 MAC addresses in the analyzed malware, which the hackers had previously stored in the malware and which should therefore be targeted if they receive an update from ASUS. To which organizations the systems selected by hackers is unknown so far.
After the infection via the malware contained in the update tool, the hackers loaded a second malware on the computers whose MAC address was included in the list. Since the command and control server is already offline and the downloaded malware could not be scanned, Kaspersky could not provide any information about its functionality and the victims.
Danger low
In spite of the large number of infected computers, Kaspersky speaks of a rather low overall risk. This is mainly due to the fact that hackers only showed real interest in a small number of systems on which the second malware was downloaded. In addition, the disappearance of the Command-and-Control Server indicates that the operation has been discontinued in the meantime.
Affected ASUS customers should nevertheless urgently update the infected software. A Tool offered free of charge by Kaspersky allows to check systems for a possible infection. To check if your MAC address is included in the malware, Kaspersky also offers a website to check. Victims of malware who want to support Kaspersky can report samples and clues to the company via E-Mail.
ASUS now also offers a Tool which allows users to check whether they have been infected by the malware. A Update of the software is also linked in a press release. The installation instructions can be found in the FAQ. As ASUS explains, several verification mechanisms have been implemented in the new software version that will make similar attacks significantly more difficult in the future.